Cloud Security
- Home
- Cloud Security
Have Any Questions?

Please Call Us
+974 4421 0929
Main Services
Regardless if you already have a well-established cloud security program or are starting your cloud migration for the first time, we can help you enhance your security strategy.
We support the development of resilient, effective, secure, and high-performing infrastructure for your applications. Security professionals that keep an eye on your infrastructure also create and maintain a wide range of cutting-edge security services that can make it easier for you to comply with your own security and regulatory standards.
Our security services and solutions are targeted at providing the following significant strategic advantages that are essential to assist you in putting your company’s ideal security posture into practice:

For a smooth and well-lanned cloud adoption strategy, define user permissions and identities, infrastructure protection, and data protection procedures.
Using logging and monitoring services, you can see how secure your company is. Add this data to a platform that can be scaled for event management, testing, and auditing.
Automated incident response and recovery can assist security teams in switching their main emphasis from responding to determining the root cause.
Utilize event-driven automation to swiftly safeguard your environment and fix it in close to real-time.
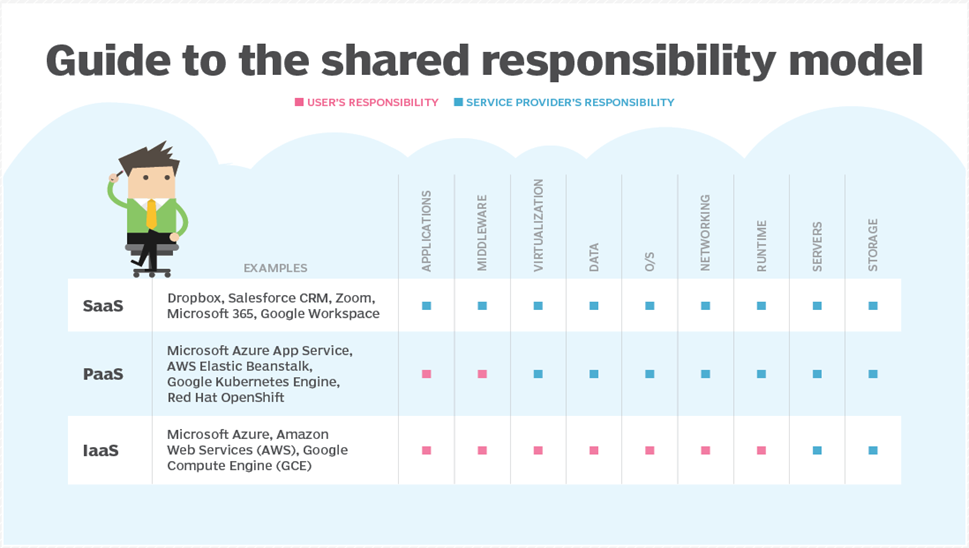
The shared responsibility model
The shared responsibility model, though not standardized, is a framework that specifies which security tasks are the responsibility of the CSP and which are the customers. To avoid coverage gaps, businesses employing cloud services must be explicit about which security duties they delegate to their provider(s) and which they must undertake internally.
Customers should always speak with their CSPs to see what is covered by the provider and what they must do on their own to protect the company.